Key Takeaways
- Understand the importance of ICMP in network communication.
- Learn about common ICMP types and how they function.
- Explore practical applications and real-world examples of ICMP in use.
- Discover how ICMP can be used to enhance network security.
Table of Contents
- What is ICMP?
- Common ICMP Messages
- ICMP in Diagnosing Network Issues
- Security Considerations Using ICMP
- Using ICMP for Network Optimization
What is ICMP?
The Internet Control Message Protocol (ICMP) is vital to the Internet Protocol Suite. It is primarily used for error messages and operational information queries between network devices. ICMP doesn’t transfer application data but is critical for diagnosing and reporting network issues. This protocol helps manage network communication through various messages that indicate success or failure in reaching another device. With such a mechanism, diagnosing network issues would be significantly more accessible, as administrators would have a way to know why or where a connection was failing. The ability to receive immediate feedback on network issues ensures that problems can be identified and resolved quickly, minimizing downtime and maintaining the network’s efficiency.
Common ICMP Messages
- Echo Request/Reply: Utilized by the “ping” command to check the reachability of a host. An Echo Request is sent to a target IP address, and if the target is reachable, an Echo Reply is received. This process helps determine whether a device is accessible over the network.
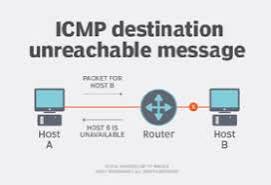
- Destination Unreachable: Informs the source that the destination cannot be reached for various reasons, such as a network being unreachable, a port being closed, or a firewall blocking the connection. This message is crucial for troubleshooting failed connections.
- Time Exceeded: This message indicates that a packet’s Time to Live (TTL) has expired. It is often used in traceroute operations to find the path packets take through the network, helping diagnose routing issues within the network.
- Redirect instructs a host to route packets through a different gateway. It is often used to optimize network traffic paths. This message helps ensure network traffic is routed through the most efficient paths, improving overall network performance.
Each message serves a unique purpose in managing and troubleshooting network operations. They enable administrators to maintain optimal network performance and quickly resolve any issues.
ICMP in Diagnosing Network Issues
Network administrators often use ICMP to diagnose connectivity issues. By sending specific messages like Echo Requests, administrators can determine the status and performance of other network devices. Some tools can capture ICMP traffic for detailed analysis. This diagnostic capability is essential for maintaining network health and performance. For example, when a website becomes inaccessible, the first step often involves sending an Echo Request to the website’s IP address. If an Echo Reply is not received, the issue could be with the website’s host server, an intermediary router, or a local network problem. Administrators can pinpoint the issue by analyzing the ICMP messages received more precisely. This functionality is particularly beneficial in large corporate networks, where pinpointing the exact location of a connectivity problem can save considerable time and resources. It also provides a clear path forward for resolving the issue, whether it requires network reconfiguration, hardware replacement, or other interventions.
Security Considerations Using ICMP
While ICMP is essential for network diagnostics, it can also be exploited in various attacks, such as ICMP Floods, which can cause a denial of service. Implementing robust security measures is crucial to mitigating these vulnerabilities. Network security professionals must balance the utility of ICMP with the need to protect against potential threats. Network administrators often implement rate-limiting and filtering rules to balance functionality and security. These measures ensure that only necessary ICMP messages are processed while protecting the network from malicious activity. For instance, many networks block incoming Echo Requests from external sources to prevent misuse while allowing internal diagnostics and performance checks.
Additionally, monitoring tools can be set up to detect unusual ICMP traffic patterns that might indicate an ongoing attack, allowing for a quick response to neutralize the threat. Security policies should also include regular reviews and updates to ensure they remain effective against evolving threats. Educating network users about potential threats and safe practices can further enhance security.
Using ICMP for Network Optimization
ICMP can also play a pivotal role in network optimization. Network administrators can regularly send Echo Request messages to gather data on latency, packet loss, and general network performance. This data informs decisions on infrastructure improvements and optimizations, ensuring reliable and speedy connections. Optimization efforts based on accurate data can significantly enhance network efficiency and user experience. For instance, ICMP can help administrators identify bottlenecks during peak usage times. Understanding where delays occur allows rapid adjustments to network paths or equipment configurations, greatly enhancing overall performance. Additionally, ICMP can help allocate bandwidth more effectively, ensuring critical applications receive the necessary resources. This proactive approach to network management allows for a more resilient network that can adapt to changing demands and conditions.
Moreover, ICMP-based monitoring can provide insights into trends and patterns in network traffic. These insights can guide long-term planning and investment in network infrastructure, helping organizations stay ahead of potential issues and maintain high-performance levels.


